The address of the remote RADIUS server x.x.x.x in remote RADIUS server group yyyyy Resolves to local address x.x.x.x.
The address will be ignored.
Use case scenario: You want to forward RADIUS requests incoming on the server to some software, possibly for setting up OTP authentication.
My scenario: Extra security for PPTP vpn tunnel to Windows server with RAS (Routing and Remote Access) by using VASCO Identikey OTP (One-Time-Passkey) software (the same applies for other software such as RSAid). Normally the recommended setup is using two servers, one for the RAS connection and one with the VASCO Identikey middleware software on it. When you deploy like this you will not face the problem I’m about to describe. However if you have only 1 Windows server at your disposal and you install the VASCO Identikey software on the same server as the RAS and NPS (Network Policy Server) role you will run in to this problem.
Problem description: You have configured RAS correctly for PPTP MSCHAP v2 connections. In NPS you have configured a connection policy to forward the RADIUS requests (authentication and accounting) to a remote RADIUS server group. The authentication fails, VASCO audit viewer does not show any attempt to authenticate to the VASCO Identikey Radius server. In the eventviewer application log there is an event ID 25 with the following error:
The address of the remote RADIUS server x.x.x.x in remote RADIUS server group yyyyy Resolves to local address x.x.x.x.
The problem is that NPS cannot forward RADIUS requests to the same IP address as itself. Even if the software is listening on another port, or you configure 2 IP addresses on the same network card. NPS insists that the IP address of the remote RADIUS server is the same as it’s own IP address and ignores your configuration to forward the RADIUS requests.
The solution is to use the loopback IP address range. For example 127.0.0.2. Unfortunately VASCO Identikey is licensed on IP address and as such you can’t change it to listen to the loopback IP address without also requesting a new license. I have not tried this, so even with the new license I’m not sure VASCO Identikey will listen on loopback IP address. Maybe other OTP software can do this, check with your vendor or manual.
What can you do? Use a RADIUS proxy to sit between the NPS and VASCO Identikey. If you have a linux server around you can use opensource FreeRadius software on that linux box to proxy the RADIUS requests between RAS/NPS and VASCO Identikey.
If like me you had nothing but this 1 windows server, you can use the FreeRadius.net software, this is a prebuilt binary of the opensource FreeRadius software made for windows versions. The software is quite old and not updated but it still seems to work for our simple setup.
I have installed the FreeRadius.net software in C:\FreeRadius.net
I have configured it to accept RADIUS requests on interface 127.0.0.2 port 11812 and forward them to a RADIUS server on IP x.x.x.x on port 18120 (I changed the default RADIUS ports for VASCO and FreeRadius to avoid conflicts with NPS/RAS).
configuration file c:\FreeRadius.net\etc\raddb\clients.conf
I have put all the default things in comment (#) and add
client 127.0.0.2 {
secret = testing123
shortname = localhost2
}
configuration file c:\FreeRadius.net\etc\raddb\radiusd.conf
I have put the default listen directive in comment (#) but you must leave the bind = * line and add
listen {
ipaddr = 127.0.0.2
port = 11812
type = auth
}
listen {
ipaddr = 127.0.0.2
port = 11813
type = acct
}
configuration file c:\FreeRadius.net\etc\raddb\proxy.conf
In this file I configured both the NULL realm for plain usernames and the DEFAULT realm for all others to forward to VASCO Identikey wich I have listening on the port 18120 & 18130 (auth & acct).
# This realm is for requests which don't have an explicit realm
# prefix or suffix. User names like "bob" will match this one.
#
realm NULL {
type = radius
authhost = 10.x.y.z:18120
accthost = 10.x.y.z:18130
secret = testing123
}
#
# This realm is for ALL OTHER requests.
#
realm DEFAULT {
type = radius
authhost = 10.x.y.z:18120
accthost = 10.x.y.z:18130
secret = testing123
}
You can now start the FreeRadius.net in debug mode, using the supplied batch file you can test your configuration.
Below I will attach screenshots of my configuration for NPS, RAS and VASCO.
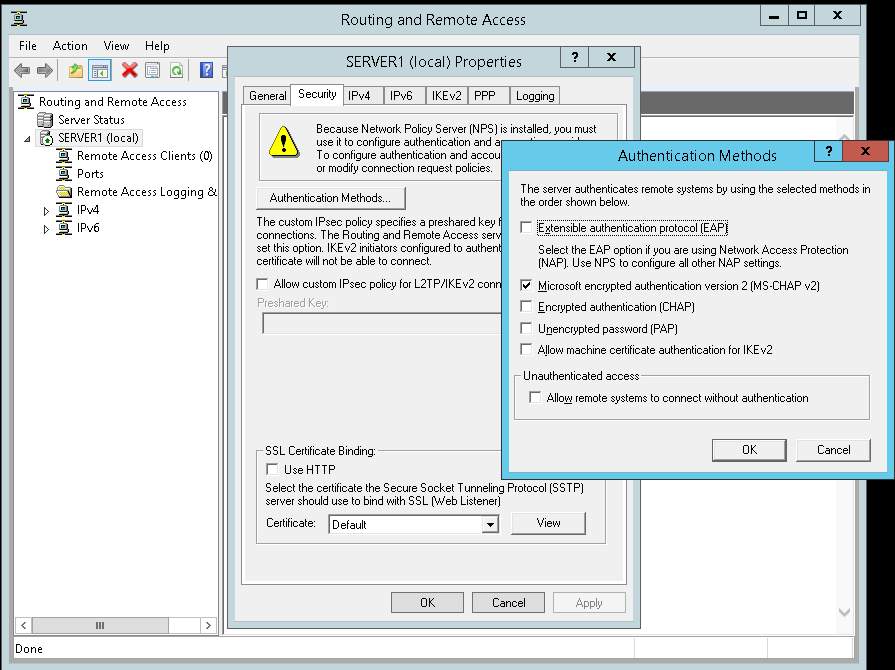
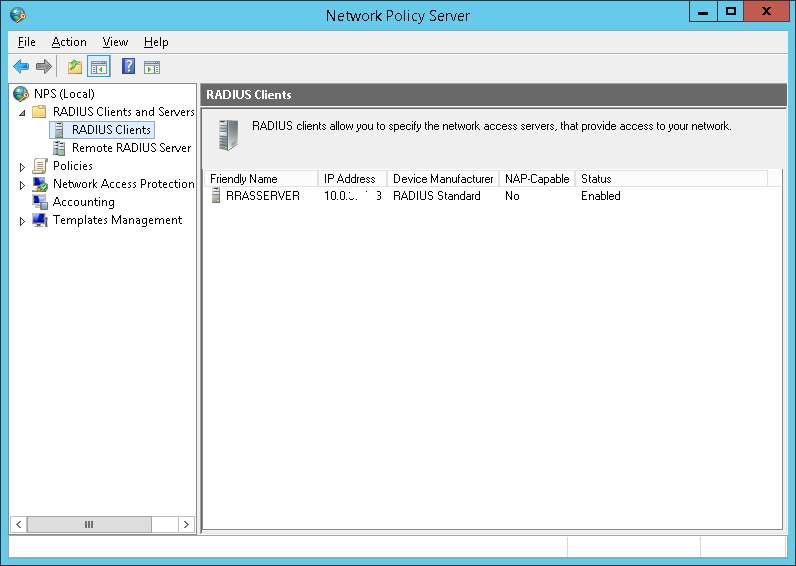

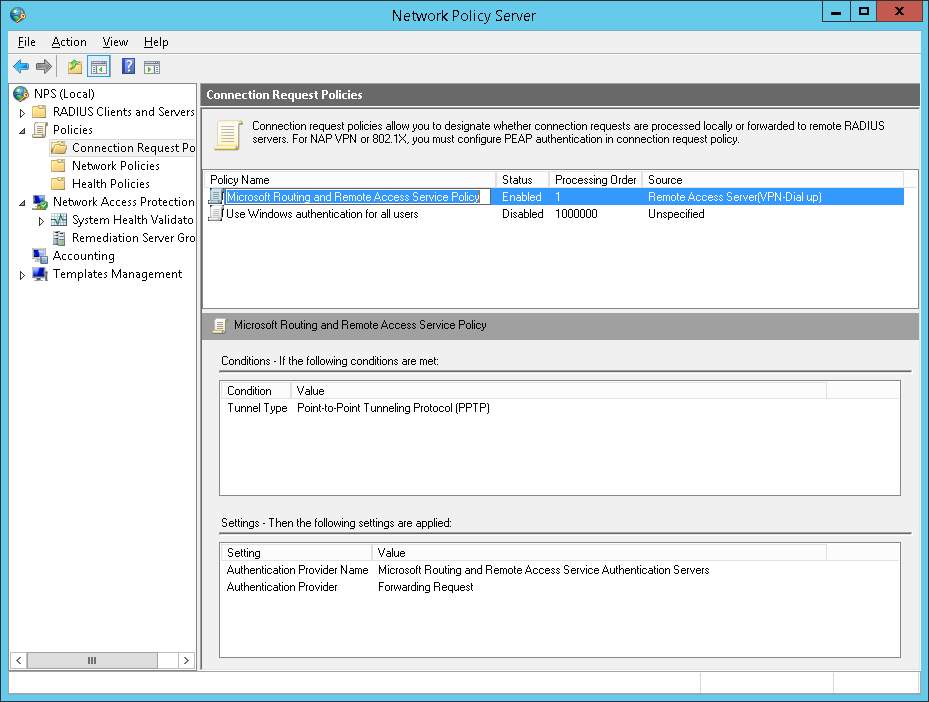
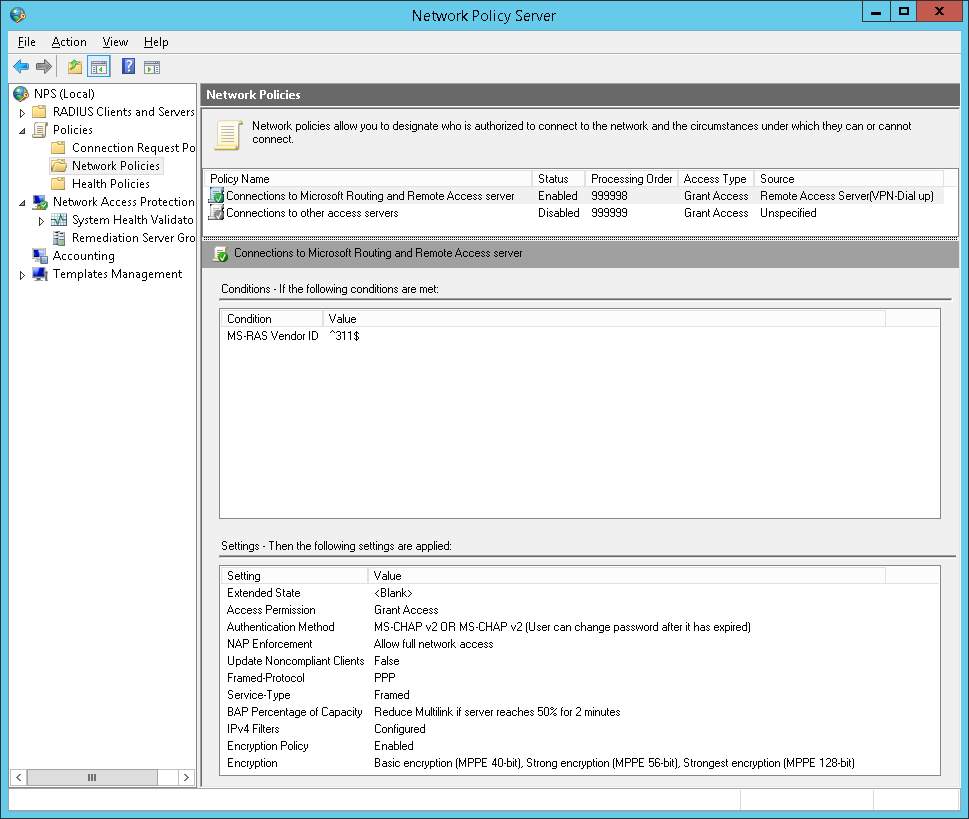
With thanks to:
http://bent-blog.de/vasco-identikey-server-auf-microsoft-forefront-tmg-2010/