Problem:
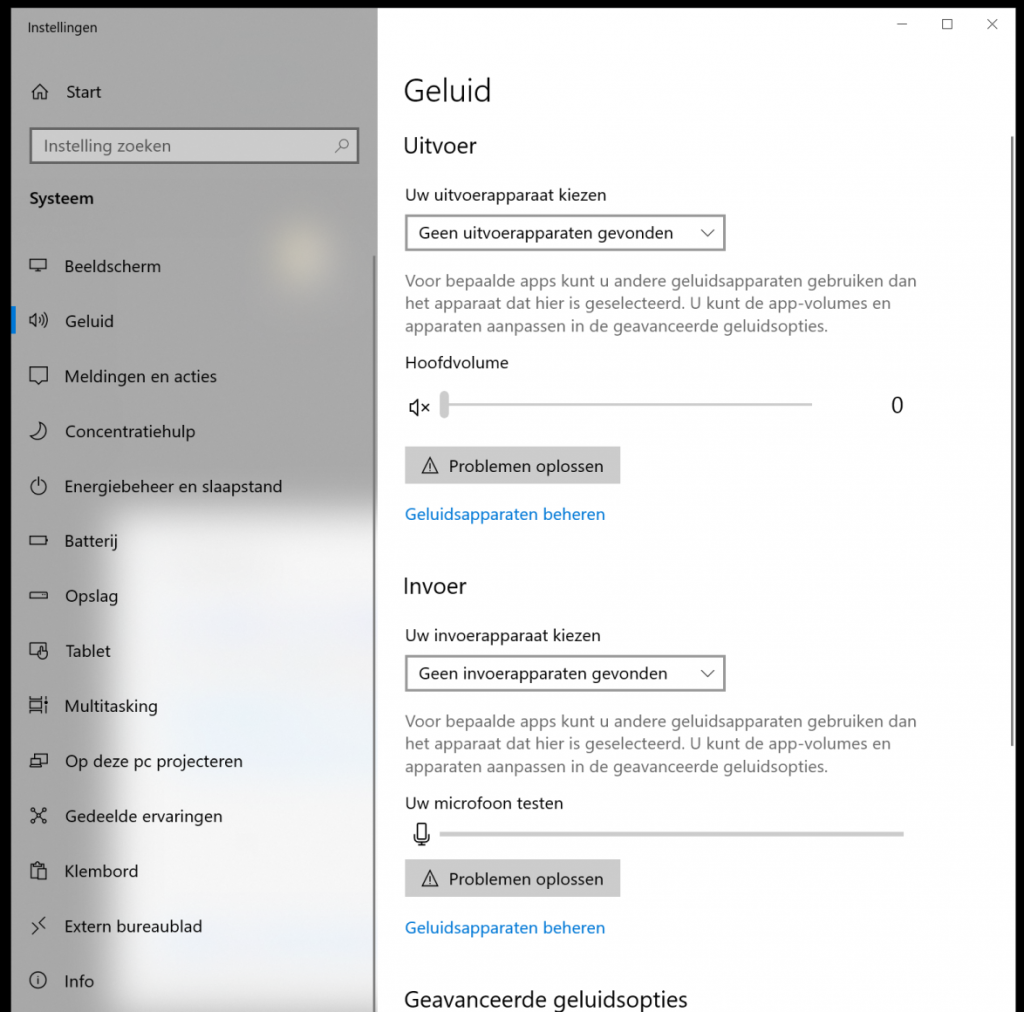
Sound is not working anymore in Windows and all programs. In the task area the speaker icon shows a red circle with an X. When you open sound settings it says there are no devices. In device manager the sound card is enabled and shows the correct latest driver.
Troubleshooting:
Removing (with delete driver) all the sound devices and output devices and reinstalling them has no effect. DISM /ScanHealth and SFC /scannow find no corruption. After trying lots of possible solutions, including doing a build upgrade to the same version, I was almost at the point that I would reset the entire system and install everything again. However in one last desperate Google search I came across the solution.
Solution:
The first solution I found was to add the localservice and networkservice (hidden) user accounts to the local administrators group. I tried this and sure enough this fixed the issue. But after reviewing other comments and checking on another (correctly working) computer I was convinced this was not a secure solution. So I removed the user accounts again from the group and sure enough the problem was back (after reboot). Luckily someone at the Dell forums found the real and secure solution.
The problem is a corrupted registry value that defines the Windows ACL rights for some part of the Windows Audio service. So open the registry editor (regedit) and navigate to the following key:HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations
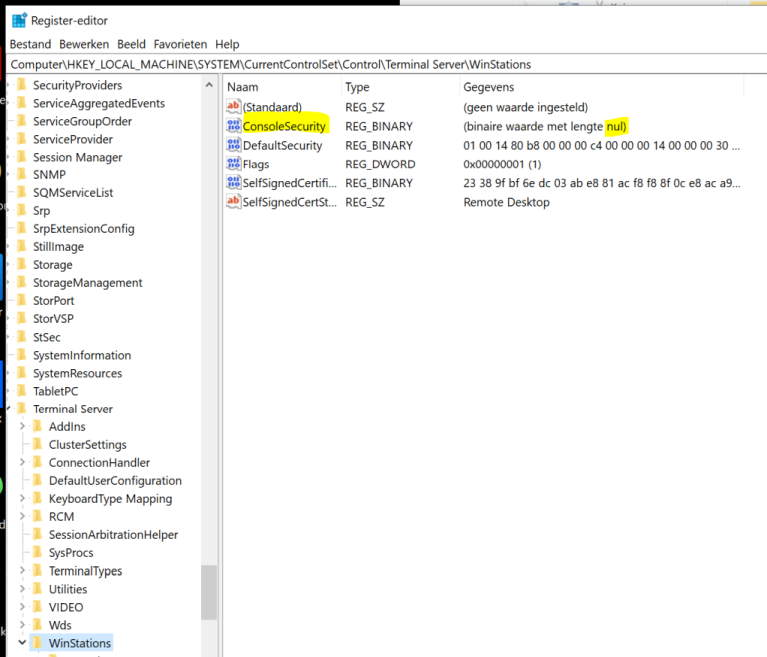
The issue is the value for ConsoleSecurity shows as binary null or empty and that’s faulty. The value is the same on each computer and should be:
"ConsoleSecurity"=hex:01,00,14,80,9c,00,00,00,a8,00,00,00,00,00,00,00,14,00,00,\
00,02,00,88,00,06,00,00,00,00,00,14,00,01,00,00,00,01,01,00,00,00,00,00,05,\
04,00,00,00,00,00,14,00,bf,03,0f,00,01,01,00,00,00,00,00,05,12,00,00,00,00,\
00,14,00,89,00,0f,00,01,01,00,00,00,00,00,05,13,00,00,00,00,00,14,00,81,00,\
00,00,01,01,00,00,00,00,00,05,14,00,00,00,00,00,18,00,bf,03,0f,00,01,02,00,\
00,00,00,00,05,20,00,00,00,20,02,00,00,00,00,18,00,21,01,00,00,01,02,00,00,\
00,00,00,05,20,00,00,00,2b,02,00,00,01,01,00,00,00,00,00,05,12,00,00,00,01,\
01,00,00,00,00,00,05,12,00,00,00I have attached a (zipped) reg file you can use to fix this value back to the original value.
More information:
Apparently this happens when the Windows 10 May 2021 cumulative update (KB5003173) fails to install the first time. Somehow in this process the registry value gets corrupted.
As a side note somehow this update failure also changes the setting in the local group policy that requires you to press CTRL-ALT-DEL at the logon screen.
Resources and credit:
https://www.dell.com/community/Latitude/Latitude-5400-no-sound-after-May-2021-Windows-update/m-p/7980056/highlight/true#M34613
https://docs.microsoft.com/en-us/answers/questions/401440/kb5003173-no-audio-device-installed.html